The main objective of network vulnerability analysis is to lower the likelihood that cybercriminals will certainly discover the weak points in your network and also exploit them, hence creating DDoS or taking your sensitive data. Network vulnerability analysis is brought out to superficially recognize main troubles as a result of which the organization would not be able, for instance, to satisfy security standards (Medical insurance Portability as well as Responsibility Act (HIPAA) if it concerns the medical care industry, Settlement Card Market Information Security Standard (PCI DSS) if it worries banking and also finance) and lug out their business operations.
Network Vulnerability Assessment And Penetration Testing
The jobs of susceptability assessment are the following: Identification, quantification and ranking of vulnerabilities located in network infrastructure, software as well as equipment systems, applications, Clarifying the effects of a theoretical situation of the uncovered protection 'holes', Establishing a technique to take on the uncovered hazards, and Providing suggestions to boost a company's safety and security posture as well as aid eliminate safety threats.
Vulnerability assessment can be performed according to the white box, black box and gray box techniques. https://www.web-directori.com/detail/9429/managed-it-service-dallas-tx.htmlThe major task a cybersecurity team requires to do when executing is to act like genuine hackers. According to this technique, the safety and security team attempts to locate means to get into the business's network 'from the exterior.' What can they see in this case? Public IP addresses, the outside user interface of a firewall software, systems situated in the demilitarized zone (DMZ), etc.
If the cybersecurity group is to carry out, they take a look at the network 'from the within,' having all the advantages of the network accredited individuals. They can see the whole connect with its documents servers, databases. The safety and security engineers have manager accessibility to all the web servers inside the network. Their goal is not simply to scan the network for vulnerabilities, but also inspect the protection of the setup of the equipments inside the network.
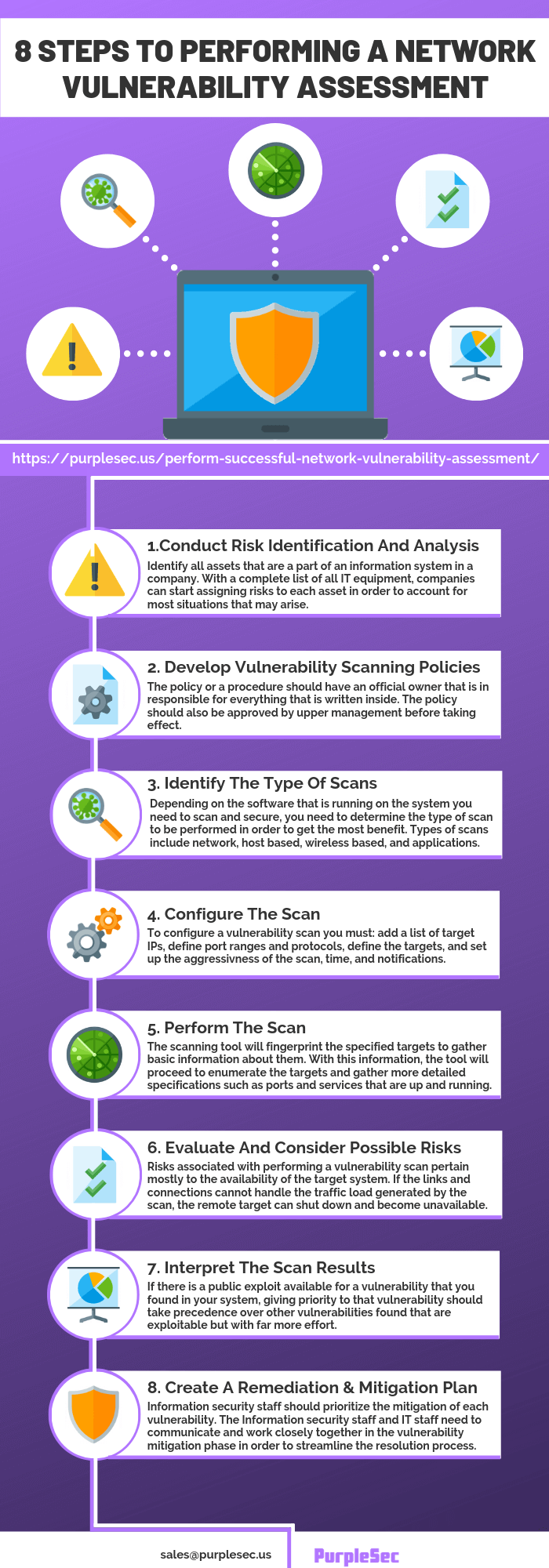
A Step-by-step Guide To Vulnerability Assessment
Security engineers carry out gray box susceptability analysis if they obtain some details on the organization's network, such as individual login details, but they don't get access to the whole network. There are pros as well as disadvantages in each method. In most companies, there are extra inner sources than those seen 'from the exterior.' When executing network susceptability assessment by 'looking about from the within,' moral cyberpunks have a broader range for action.
Susceptability analysis is done with automated scanning tools that give the scanning results with the checklists of vulnerabilities, typically focused on by their severity. There are two kinds of vulnerability assessment tools (scanners) as well as, which work nearly in the exact same method. Both open resource and also commercial susceptability assessment tools function on the basis of with control specifications, for the conformity with which the network is being checked.
The bottom lines both kinds of network susceptability evaluation tools vary from each various other are listed here: Open up resource vulnerability evaluation tools do not call for licensing, unlike commercial ones. When buying a business scanning tool, a susceptability evaluation vendor spends for software program, employees training, in addition to for a permit.
The Art Of Network Vulnerability Assessment
For that reason, it's obvious that the expense of network vulnerability analysis solutions may rise immensely for a consumer that makes a decision to get such services executed with business scanning devices. When the scanning is over, protection engineers obtain records having the uncovered susceptabilities. Industrial tools give even more insightful searchings for with less false-positives (the found susceptabilities that do not actually exist).
Business devices are upgraded a lot more often than open resource ones. When the data source of a scanning tool obtains updates, one of the most just recently uncovered protection susceptabilities are included to it. An upgrading procedure of a scanning tool's database executed regularly dramatically improves the likelihood that the prospective susceptabilities in the company's network will certainly be identified.
There's also an option for a scanning device to be integrated as an into a SIEM system. As an example, IBM QRadar SIEM can be matched with the following susceptability assessment modules: Danger Supervisor, Vulnerability Supervisor as well as Event Forensics, which makes it a multi-purpose option.
Network Vulnerability Assessment
The cybersecurity group determined the way company procedures were performed in the company and agreed with the client on the evaluation goals, the extent of job. The organization required to spot protection problems and carry out restorative actions to end up being PCI DSS certified. So, the security engineers were charged with executing vulnerability assessment for the organization's internal subnetworks.
More particularly, the team specified whether the network had open ports or solutions that should not be opened up, obtained the understanding of the software program as well as motorists arrangements, found out whether the logs from the network services are sent out to a safety and security details and also event management (SIEM) remedy. They likewise identified virtual and also physical web servers, as well as the protection measures that were already in area, such as firewalls as well as invasion discovery and avoidance systems (IPS/IDS).
It permitted to uncover the internet server version, examine the web servers to make certain that their ports are running effectively, ping network sectors. Thus, the security team checked target subnetworks to fingerprint running services and also running systems. For that, they sent demands to the hosts (computer systems or digital makers) being checked as well as assessed their reactions.